RV042 - disable split tunneling
Hi all
I am currently using a firewall RV042 linked to an another RV042 via the VPN Site to Site.
Everything works fine and dandy, however, I want to disable internet access on one of the RV042s.
Is there a way I can disable the split on the RV042 tunneling to achieve? It doesn't seem to be what I can find on the menus that claim.
Looking forward to some counselor here.
Thank you!
jag_lin84,
The firewall allows all outbound traffic and blocks all incoming traffic by default. You can create an access rule to block all outbound traffic.
Action: reject
Service: all the
Newspaper: -.
Source interface: LAN
Source IP: no
Destination IP: all
-Marty
Tags: Cisco Support
Similar Questions
-
Disable Split Tunneling - SAs are not when I change crypto ACL
Hello!
When I change my ACL Crypto I receive an error message in phase I: "PROPOSAL_NOT_CHOSEN NOTIFIER' of IKE. I do this to disable the ST and get all the hollow tunnel traffic. Please see the config below:
crypto ISAKMP policy 10
md5 hash
preshared authentication
life 3600
ISAKMP crypto key cisco address x.x.x.x
!
!
Crypto ipsec transform-set esp - the esp-hmac-md5 ENCRYPTION
!
crypto map ipsec-isakmp CLIENT 1
defined peer x.x.x.x
game of transformation-CRYPTO
match address 115
!
access-list 115 permit ip 10.10.10.0 0.0.0.255 10.10.11.0 0.0.0.255
access-list 115 deny ip any one
I changed the ACL 115 to so I can disable split tunneling, and it looks like this:
access-list 115 permit ip 10.10.10.0 0.0.0.255 any
access-list 115 deny ip any one
What is a failure? I have donthink the crypto ACL must be the same?
OK, you use a card dynamic encryption on your head just as I suggested, so that's fine. What you have done, which is causing your problem (and usually causes more problems than it's worth), is to assign an access list to the dynamic encryption card. It is not necessary, because with a dynamic encryption the router head card accept any model of traffic the remote router sends.
In your case since you changed the remote router to be 'all', it is no longer maps to the 115 ACL on the head and now is failing.
Way easier around it is simply to remove the 'match 115' address card dynamic encryption on the head. This will not affect any of your other tunnels and allow the remote router to establish a tunnel.
The exact commands you would use are as follows:
> crypto dynamic-map PERSONAL 10
> no address for correspondence 115
-
Access restricted without the split tunneling
I'm disabled with Split tunneling VPN concentrator. Split tunneling has been disabled to carry the internet traffic of vpn clients via our internal web filtering server. But I must restrict access to my internal servers. How can I do that. I tried with filters/Rules but his does not work, and depending on the traffic of documents filter applies only to the traffic unencrypted.
Thank you
Avil
If you use a VPN3000 while you can apply a filter to the users configured in group. This filter can restrict access to the servers as a list of specific protocols and access. This filter certainly applies to ENCRYPTED traffic, do not know what you are referring to your last sentence.
You must first define the rules to define the traffic you want to restrict address., see here for more details:
http://www.Cisco.com/univercd/CC/TD/doc/product/VPN/vpn3000/4_1/config/polmgt.htm#1321359
Define a filter, then add the rules you just set it to him:
http://www.Cisco.com/univercd/CC/TD/doc/product/VPN/vpn3000/4_1/config/polmgt.htm#1007037
Thne go under the group that these users are configured with, and then apply the filter to it.
A couple of sample filter are the following:
Allow access to 10.1.1.2 and block everything else:
To block access to everything, but 10.10.1.2, create a rule that is Inbound/Forward, Source of Anything, Destination of 10.1.1.2/0.0.0.0. Create another rule, it can be left at the default value which is incoming, drop, no matter what Source Dest what whatsoever. Create a filter with the default action of the front and add two new your rules, ensuring that rule that allows access to the host 10.1.12 is above the default rule which will pass everything else.
Block access to 10.1.1.2, and leave all the rest:
To allow access to everything except 10.10.1.2, create a rule that said, drop, no matter what Source and Destination of 10.10.1.2/0.0.0.0. Add a filter that has a default action is to send, add the rule to the filter.
Notes:
-You can allow or block access to subnets simply by changing your address/mask to something like combination: 10.1.1.0/0.0.0.255
-
Windows - Internet access, no split Tunnel L2TP VPN Clients does not
Greetings!
I have four ASA 5505 that I configured with 4 site to site VPN tunnels (works perfectly) to connect to our company facilities 4. The ASA is also configured with remote access L2TP/IPsec so that a specific group of users of portable computers can connect to and access to all facilities. It also works very well except for one important exception - my split tunnel setting doesn't seem to work, because I can't connect to the Internet outside the VPN resources.
I accept the inherent risk of allowing tunnels to split from a security point of view since I take the necessary steps to secure the systems used for remote access. I would appreciate any feedback on how to get the job of split tunnel.
Here is the configuration:
: Saved
:
ASA Version 1.0000 11
!
SGC hostname
domain somewhere.com
names of
COMMENTS COMMENTS LAN 192.168.2.0 name description
name 75.185.129.13 description of SGC - external INTERNAL ASA
name 172.22.0.0 description of SITE1-LAN Ohio management network
description of SITE2-LAN name 172.23.0.0 Lake Club Network
name 172.24.0.0 description of training3-LAN network Southwood
description of training3 - ASA 123.234.8.124 ASA Southwoods name
INTERNAL name 192.168.10.0 network Local INTERNAL description
description of name 192.168.11.0 INTERNAL - VPN VPN INTERNAL Clients
description of Apollo name 192.168.10.4 INTERNAL domain controller
description of DHD name 192.168.10.2 Access Point #1
description of GDO name 192.168.10.3 Access Point #2
description of Odyssey name 192.168.10.5 INTERNAL Test Server
CMS internal description INTERNAL ASA name 192.168.10.1
name 123.234.8.60 description of SITE1 - ASA ASA management Ohio
description of SITE2 - ASA 123.234.8.189 Lake Club ASA name
description of training3-VOICE name Southwood Voice Network 10.1.0.0
name 172.25.0.0 description of training3-WIFI wireless Southwood
!
interface Vlan1
nameif outside
security-level 0
IP address dhcp setroute
!
interface Vlan2
nameif INSIDE
security-level 100
255.255.255.0 SGC-internal IP address
!
interface Vlan3
nameif COMMENTS
security-level 50
IP 192.168.2.1 255.255.255.0
!
interface Ethernet0/0
Time Warner Cable description
!
interface Ethernet0/1
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/2
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/3
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/4
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/5
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/6
Description for Wireless AP Trunk Port
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
interface Ethernet0/7
Description for Wireless AP Trunk Port
switchport access vlan 2
switchport trunk allowed vlan 2-3
switchport vlan trunk native 2
switchport mode trunk
!
boot system Disk0: / asa821-11 - k8.bin
Disk0: / config.txt boot configuration
passive FTP mode
clock timezone IS - 5
clock to summer time EDT recurring
DNS domain-lookup outside
INTERNAL DNS domain-lookup
DNS domain-lookup GUEST
DNS server-group DefaultDNS
Name-Server 4.2.2.2
domain somewhere.com
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
DM_INLINE_TCP_1 tcp service object-group
EQ port 3389 object
port-object eq www
EQ object of the https port
EQ smtp port object
the DM_INLINE_NETWORK_1 object-group network
network-object SITE1-LAN 255.255.0.0
network-object SITE2-LAN 255.255.0.0
network-object training3-LAN 255.255.0.0
object-group training3-GLOBAL network
Southwood description Global Network
network-object training3-LAN 255.255.0.0
network-object training3-VOICE 255.255.0.0
network-object training3-WIFI 255.255.0.0
DM_INLINE_TCP_2 tcp service object-group
EQ port 5900 object
EQ object Port 5901
object-group network INTERNAL GLOBAL
Description Global INTERNAL Network
network-object INTERNAL 255.255.255.0
network-object INTERNALLY-VPN 255.255.255.0
access-list outside_access note Pings allow
outside_access list extended access permit icmp any CMS-external host
access-list outside_access note that VNC for Camille
outside_access list extended access permit tcp any host CMS-external object-group DM_INLINE_TCP_2
access-list outside_access note INTERNAL Services
outside_access list extended access permit tcp any host CMS-external object-group DM_INLINE_TCP_1
DefaultRAGroup_splitTunnelAcl list standard access allowed INTERNAL 255.255.255.0
access-list sheep extended ip INTERNAL 255.255.255.0 allow INTERNAL VPN 255.255.255.0
access-list extended sheep allowed ip IN-HOUSE-GLOBAL SITE1-LAN 255.255.0.0 object-group
access-list extended sheep allowed ip IN-HOUSE-GLOBAL SITE2-LAN 255.255.0.0 object-group
access-list extended sheep allowed ip object-IN-HOUSE-GLOBAL object group training3-GLOBAL
access-list INTERNAL-to-SITE1 extended permit ip IN-HOUSE-GLOBAL SITE1-LAN 255.255.0.0 object-group
access-list INTERNAL-to-training3 extended permitted ip object-IN-HOUSE-GLOBAL object group training3-GLOBAL
access-list INTERNAL-to-SITE2 extended permit ip IN-HOUSE-GLOBAL SITE2-LAN 255.255.0.0 object-group
no pager
Enable logging
exploitation forest asdm warnings
Debugging trace record
Outside 1500 MTU
MTU 1500 INTERNAL
MTU 1500 COMMENTS
192.168.11.1 mask - local 192.168.11.25 pool IN-HOUSE VPN IP 255.255.255.0
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 623.bin
enable ASDM history
ARP timeout 14400
Global 1 interface (outside)
(INTERNAL) NAT 0 access-list sheep
NAT (INTERNAL) 1 0.0.0.0 0.0.0.0
NAT (GUEST) 1 0.0.0.0 0.0.0.0
5900 5900 Camille netmask 255.255.255.255 interface static tcp (GUEST, outdoor)
3389 3389 Apollo netmask 255.255.255.255 interface static tcp (INDOOR, outdoor)
public static tcp (INDOOR, outdoor) interface www Apollo www netmask 255.255.255.255
public static tcp (INDOOR, outdoor) interface https Apollo https netmask 255.255.255.255
public static tcp (INDOOR, outdoor) interface smtp smtp Apollo netmask 255.255.255.255
5901 puppy 5901 netmask 255.255.255.255 interface static tcp (GUEST, outdoor)
Access-group outside_access in interface outside
Timeout xlate 0:05:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
RADIUS protocol AAA-server Apollo
Apollo (INTERNAL) AAA-server Apollo
Timeout 5
key *.
AAA authentication enable LOCAL console
the ssh LOCAL console AAA authentication
AAA authentication LOCAL telnet console
AAA authentication http LOCAL console
Enable http server
http 0.0.0.0 0.0.0.0 INTERNAL
http 0.0.0.0 0.0.0.0 COMMENTS
No snmp server location
No snmp Server contact
Community SNMP-server
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac TRANS_ESP_3DES_SHA
Crypto ipsec transform-set transit mode TRANS_ESP_3DES_SHA
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
SYSTEM_DEFAULT_CRYPTO_MAP game 65535 dynamic-map crypto transform-set ESP-3DES-SHA TRANS_ESP_3DES_SHA
correspondence address 1 card crypto outside_map INTERNAL SITE1
card crypto outside_map 1 set of peer SITE1 - ASA
card crypto outside_map 1 set of transformation-ESP-3DES-SHA
address for correspondence card crypto outside_map 2 INTERNAL training3
outside_map 2 peer training3 - ASA crypto card game
card crypto outside_map 2 game of transformation-ESP-3DES-SHA
address for correspondence outside_map 3 card crypto INTERNAL SITE2
game card crypto outside_map 3 peers SITE2 - ASA
card crypto outside_map 3 game of transformation-ESP-3DES-SHA
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
delimiter group @.
Telnet training3 - ASA 255.255.255.255 outside
Telnet SITE2 - ASA 255.255.255.255 outside
Telnet SITE1 - ASA 255.255.255.255 outside
Telnet 0.0.0.0 0.0.0.0 INTERNAL
Telnet 0.0.0.0 0.0.0.0 COMMENTS
Telnet timeout 60
SSH enable ibou
SSH training3 - ASA 255.255.255.255 outside
SSH SITE2 - ASA 255.255.255.255 outside
SSH SITE1 - ASA 255.255.255.255 outside
SSH 0.0.0.0 0.0.0.0 INTERNAL
SSH 0.0.0.0 0.0.0.0 COMMENTS
SSH timeout 60
Console timeout 0
access to the INTERNAL administration
Hello to tunnel L2TP 100
interface ID client DHCP-client to the outside
dhcpd dns 4.2.2.1 4.2.2.2
dhcpd ping_timeout 750
dhcpd outside auto_config
!
address INTERNAL 192.168.10.100 dhcpd - 192.168.10.200
dhcpd Apollo Odyssey interface INTERNAL dns
dhcpd somewhere.com domain INTERNAL interface
interface of dhcpd option 150 ip 10.1.1.40 INTERNAL
enable dhcpd INTERNAL
!
dhcpd address 192.168.2.100 - 192.168.2.200 COMMENTS
dhcpd dns 4.2.2.1 4.2.2.2 interface COMMENTS
enable dhcpd COMMENTS
!a basic threat threat detection
statistical threat detection port
Statistical threat detection Protocol
Statistics-list of access threat detection
a statistical threat detection tcp-interception rate-interval 30 burst-400-rate average rate 200
NTP server 192.43.244.18 prefer external source
WebVPN
allow outside
CSD image disk0:/securedesktop-asa-3.4.2048.pkg
SVC disk0:/sslclient-win-1.1.4.179.pkg 1 image
SVC disk0:/anyconnect-win-2.4.1012-k9.pkg 2 image
enable SVC
Group Policy DefaultRAGroup INTERNAL
attributes of Group Policy DefaultRAGroup
Server DNS 192.168.10.4 value
Protocol-tunnel-VPN l2tp ipsec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list DefaultRAGroup_splitTunnelAcl
value by default-domain somewhere.com
Group Policy DefaultWEBVPNGroup INTERNAL
attributes of Group Policy DefaultWEBVPNGroup
VPN-tunnel-Protocol webvpn
Group Policy DefaultL2LGroup INTERNAL
attributes of Group Policy DefaultL2LGroup
Protocol-tunnel-VPN IPSec l2tp ipsec
Group Policy DefaultACVPNGroup INTERNAL
attributes of Group Policy DefaultACVPNGroup
VPN-tunnel-Protocol svc
attributes of Group Policy DfltGrpPolicy
value of 192.168.10.4 DNS Server 4.2.2.2
VPN - 25 simultaneous connections
VPN-idle-timeout no
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list DefaultRAGroup_splitTunnelAcl
value by default-domain somewhere.com
the value INTERNAL VPN address pools
chip-removal-disconnect disable card
WebVPN
SVC keepalive no
client of dpd-interval SVC no
dpd-interval SVC bridge no
value of customization DfltCustomization
attributes global-tunnel-group DefaultRAGroup
VPN INTERNAL address pool
Group Policy - by default-DefaultRAGroup
IPSec-attributes tunnel-group DefaultRAGroup
pre-shared-key *.
Disable ISAKMP keepalive
tunnel-group DefaultRAGroup ppp-attributes
No chap authentication
no authentication ms-chap-v1
ms-chap-v2 authentication
attributes global-tunnel-group DefaultWEBVPNGroup
VPN INTERNAL address pool
Group Policy - by default-DefaultWEBVPNGroup
tunnel-group 123.234.8.60 type ipsec-l2l
IPSec-attributes tunnel-group 123.234.8.60
pre-shared-key *.
tunnel-group 123.234.8.124 type ipsec-l2l
IPSec-attributes tunnel-group 123.234.8.124
pre-shared-key *.
tunnel-group 123.234.8.189 type ipsec-l2l
IPSec-attributes tunnel-group 123.234.8.189
pre-shared-key *.
type tunnel-group DefaultACVPNGroup remote access
attributes global-tunnel-group DefaultACVPNGroup
VPN INTERNAL address pool
Group Policy - by default-DefaultACVPNGroup
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
inspect the http
inspect the they
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:423c807c0d63cb3e9aeceda977053f84
: end
ASDM image disk0: / asdm - 623.bin
ASDM location Camille 255.255.255.255 INTERNAL
ASDM location INTERNAL CGT-external 255.255.255.255
ASDM location INTERNAL SITE1-LAN 255.255.0.0
ASDM location INTERNAL SITE2-LAN 255.255.0.0
ASDM location INTERNAL training3-LAN 255.255.0.0
ASDM location INTERNAL training3 - ASA 255.255.255.255
ASDM location INTERNAL GDO 255.255.255.255
ASDM location INTERNAL SITE1 - ASA 255.255.255.255
ASDM location INTERNAL SITE2 - ASA 255.255.255.255
ASDM location INTERNAL training3-VOICE 255.255.0.0
ASDM location puppy 255.255.255.255 INTERNAL
enable ASDM historyI should also mention that my test clients are a combination of Windows XP, Windows 7, and Windows Mobile. Other that in specifying the preshared key and forcing L2TP/IPsec on the client side, the VPN settings on clients are the default settings with the help of MS-CHAP/MS-CHAPv2.
You must configure * intercept-dhcp enable * in your group strategy:
attributes of Group Policy DefaultRAGroup
attributes of Group Policy DefaultRAGroup
Server DNS 192.168.10.4 value
Protocol-tunnel-VPN l2tp ipsec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list DefaultRAGroup_splitTunnelAcl
value by default-domain somewhere.comIntercept-dhcp enable
-Latptop VPN clients (which I assume are on windows computers) is also the * use on remote network default gateway * box unchecked. It is located on the Advanced tab of VPN client TCP/IP properties. Select Client VPN > properties > Networking > TCP/IP Internet Protocol > properties > advanced and uncheck the box.
Alex
-
No split tunnel-access internet via isa in dmz
Hello
I have configured my asa 5520 v 7.2 for remote VPN. Its works fine. I need to provide my customer internet access without activating split tunnel. I went through a few example below of a doc:
the preceding is not enough more me like one have different needs
I want my client VPN to ASA and access to internet, I had ISA connected to the VPN device. All my vpn clients want access to the internet, it must use this operation to access the internet. My ISA server is in the same subnet of the VPN device by using a different gw for internet access.
Pls comment
Add the below: -.
attributes of the strategy of group staffvpn
use a MSIE-proxy-server method
Internet Explorer-proxy server value x.x.x.x
Disable Internet Explorer-proxy local-bypass
attributes of the strategy of group staffvpn
use a MSIE-proxy-server method
Internet Explorer-proxy server value x.x.x.x
Disable Internet Explorer-proxy local-bypass
attributes of the strategy of group newstaffvpn
use a MSIE-proxy-server method
Internet Explorer-proxy server value x.x.x.x
Disable Internet Explorer-proxy local-bypass
adel username attributes
use a MSIE-proxy-server method
Internet Explorer-proxy server value x.x.x.x
Disable Internet Explorer-proxy local-bypass
username weppe attributes
use a MSIE-proxy-server method
Internet Explorer-proxy server value x.x.x.x
Disable Internet Explorer-proxy local-bypass
Remote VPN group no matter what you want to test with. where x.x.x.x is the IP address of the ISA server computer.
HTH.
-
Split tunnel with ASA 5510 and PIX506.
Hello
I have the production between Asa 5510 (main office) and Pix 506 VPN tunnel. It is configured so that all traffic is encrypted and moves through the tunnel. This includes remote users behind Pix Internet traffic. I would like to use split tunnel and direct Internet traffic hitting the web directly from Pix instead of going through the tunnel. How can I do this safely? Please see current config Pix below:
:
6.3 (5) PIX version
interface ethernet0 car
interface ethernet1 10baset
ethernet0 nameif outside security0
nameif ethernet1 inside the security100clock timezone EDT - 5
clock to summer time EDT recurring 2 Sun Mar 2:00 1 Sun Nov 02:00
No fixup protocol dns
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol they 389
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
No fixup protocol sip udp 5060
fixup protocol 2000 skinny
fixup protocol smtp 25
fixup protocol sqlnet 1521
no correction protocol tftp 69
names of
allow VPN 192.x.x.x 255.255.255.0 ip access list one
LocalNet ip access list allow a whole
pager lines 20
opening of session
monitor debug logging
logging warnings put in buffered memory
logging trap warnings
Outside 1500 MTU
Within 1500 MTU
IP address outside 24.x.x.x 255.255.255.0
IP address inside192.x.x.x 255.255.255.0
IP audit name Outside_Attack attack action alarm down reset
IP audit name Outside_Recon info action alarm down reset
interface IP outside the Outside_Recon check
interface IP outside the Outside_Attack check
alarm action IP verification of information
reset the IP audit attack alarm drop action
disable signing verification IP 2000
disable signing verification IP 2001
disable signing verification IP 2004
disable signing verification IP 2005
disable signing verification IP 2150
PDM logging 100 information
history of PDM activate
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0 access-list LocalNet
Route outside 0.0.0.0 0.0.0.0 24.x.x.x
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Sip timeout - disconnect 0:02:00 prompt Protocol sip-0: 03:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
AAA-server GANYMEDE + 3 max-failed-attempts
AAA-server GANYMEDE + deadtime 10
RADIUS Protocol RADIUS AAA server
AAA-server RADIUS 3 max-failed-attempts
AAA-RADIUS deadtime 10 Server
AAA-server local LOCAL Protocol
Enable http server
enable floodguard
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac AMC
map UrgentCare 10 ipsec-isakmp crypto
card crypto UrgentCare 10 corresponds to the VPN address
card crypto UrgentCare 10 set counterpart x.x.x.x
card crypto UrgentCare 10 value transform-set AMC
UrgentCare interface card crypto outside
ISAKMP allows outside
ISAKMP key * address x.x.x.x 255.255.255.255 netmask
ISAKMP identity address
part of pre authentication ISAKMP policy 20
ISAKMP policy 20 3des encryption
ISAKMP policy 20 md5 hash
20 2 ISAKMP policy group
ISAKMP duration strategy of life 20 86400
SSH timeout 15
Console timeout 0
Terminal width 80
Cryptochecksum:9701c306b05151471c437f29695ffdbd
: endI would do something by changing the acl that applies to your crypto card. You want to know what you want to support above the tunnel and then deny other networks.
If you have:
192.168.3.0/24
192.168.4.0/24
10.10.10.0/24
172.16.0.0/16
Do something like:
VPN access list allow 192.x.x.x ip 255.255.255.0 192.168.3.0 255.255.255.0
VPN access list allow 192.x.x.x ip 255.255.255.0 192.168.4.0 255.255.255.0
VPN access list allow 192.x.x.x ip 255.255.255.0 10.10.10.0 255.255.255.0
VPN access list allow 192.x.x.x 255.255.255.0 ip 172.16.0.0 255.255.0.0
Then when the traffic is destined for something other than these networks, it will go not to the ISP instead of the tunnel.
HTH,
John
-
Hello.
All started to play with split-mining.
So far so good.
I can access the server when the Tunnel of splitting is disabled, and my itinerary looks very good. But cannot access the internet.
I can not access the server when the Tunnel of splitting is enabled, my itinerary seems wrong. But can access the internet.
I think it's my access list the problem (also tried to overthrow).
split_test list extended access allowed host 4.4.4.4 ip 10.10.253.0 255.255.255.0
attributes of the strategy of group test_policy
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list split_test
I read that I can't filter on the ports during the shared use of tunnelling, is this correct?
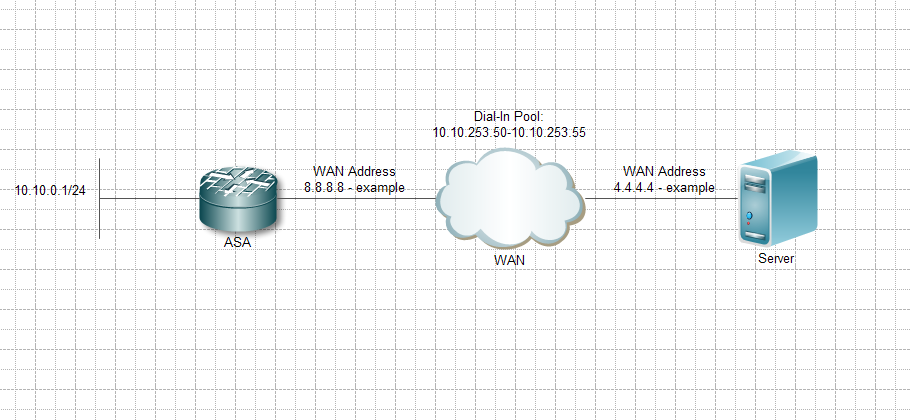
I have attached a quick drawing of the installation.
Best regards, Søren.
Hello
Then you can use the following version of above indicate changes in configurations
attributes of the strategy of group test_policy
No split-tunnel-network-list split_test value
No list of extended split_test access not allowed host 4.4.4.4 ip 10.10.253.0 255.255.255.0
host of access TUNNEL of SPLIT standard allowed 4.4.4.4 list
attributes of the strategy of group test_policy
no value of split-tunnel-network-list SPLIT-TUNNEL
The above configuration would be basically set up the VPN Client connection so that connections for ONLY the IP 4.4.4.4 the VPN connection will be provided by the user.
As I understand it, the traffic of users to the destination server would only be encrypted between the Client and the ASA. From there it would be just like any traffic between hosts on the external network. Except of course your ASA has a separate VPN L2L connection on the site where the Server 4.4.4.4.
Even if the above Split Tunnel ACL configuration is correct, you will still need to manage the NAT for VPN Client users. To determine the NAT configuration correct, I need to know the version of the software of your ASA and the current dynamic PAT rule for internal users, for example if the VPN users are supposed to use the same public IP address for their IP NAT address.
Also, you will at least have to add this configuration on the SAA
permit same-security-traffic intra-interface
This will allow connections to VPN users enter through the 'outside' of the interface and head to this same ' outside ' interface. It is not possible without the above configured command even if all other configurations were correct.
-Jouni
Post edited by: Jouni Forss (typos in the post)
-
I'm working on an installation of the laboratory program at home with my X-5506, and I got a split tunneling configuration problem. Every change I seem to give me internet access, gives me access to the local network or remove both. The current configuration, I took them both and I am a little puzzled. I have attached the configuration. Any guidance would be greatly appreciated!
Change:
split-tunnel-policy excludespecified
TO:split-tunnel-policy tunnelspecified
I notice you are using 192.168.0.0/24. Make sure that you do not work VPN'ing an address 192.168.0.0/24 as well (or a subnet that is also identical to your subnet that you are trying to access remotely) or it won't work. Overall, you should avoid using 10.0.0.0/24 and 192.168.0.0/24 in production networks because they are so frequently used in home networks. I also note that you have configured IKEv2. IKEv2 does not support split tunneling. SO be sure you use only the AnyConnect client in SSL mode. -
Cisco ASA ruled out a specific ip address of the split tunneling
Hello
I need help with a question on the split Tunneling Configuration.
I have need exclude split tunneling networks already configured a specific ip address.
This is my setup:
Split_Tunnel list standard access allowed 192.168.0.0 255.255.0.0
Split_Tunnel list standard access allowed 10.0.0.0 255.0.0.0attributes of Group Policy GroupPolicy_Anyconnect_Access_Exception_1
WINS server no
Server DNS value xxxxx xxxxxxx
VPN - connections 3
VPN-idle-timeout 480
VPN-session-timeout no
client ssl-VPN-tunnel-Protocol
value of group-lock Anyconnect_access
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list Split_Tunnel
field default value xxxxx
Split-dns value telefonica wh.telefonica cic.wh.telefonica telefonica.corp t380.inet
mailar.telefonica.Corp mailar.telefonica.com tefgad.com telefonicaglobalsolutions.com
telefonicabusinesssolutions.comI need to exclude the split tunnel, IP 10.0.0.50, my question is, if I change the list access deny this IP, the supplementary tunnel will exclude the period of INVESTIGATION.
example:
Split_Tunnel list standard access deny 10.0.0.50 255.255.255.255
Split_Tunnel list standard access allowed 192.168.0.0 255.255.0.0
Split_Tunnel list standard access allowed 10.0.0.0 255.0.0.0BR,
Fidel Gonzalez
Hi Fidel,
Yes, it should work; as in your example deny 10.0.0.50/32 sholud exclude the traffic in the tunnel.
I tried in my lab, and in my case, access-list is:
split_1 list standard access denied the host 10.2.2.250
split_1 list standard access allowed 10.2.2.0 255.255.255.0And it worked he excluded the 10.2.2.250 host.
The screen shot of the AnyConnect added:
Concerning
Véronique
-
Easy VPN between two ASA 9.5 - Split tunnel does not
Hi guys,.
We have set up a site to site vpn using easy configuration vpn between ver 9.5 race (1) two ASA. The tunnels are up and ping is reached between sites. I also configured split tunnel for internet traffic under the overall strategy of the ASA easy vpn server. But for some unknown reason all the customer same internet traffic is sent to the primary site. I have configured NAT to relieve on the side of server and client-side. Please advise if no limitation so that the installation program.
Thank you and best regards,
Arjun T P
I have the same question and open a support case.
It's a bug in the software 9.5.1. See the bug: CSCuw22886
-
Hi guys,.
I just sent a SRP527W that I had lying around for a while.
Everything about the unit works as well as can be expected, however I have an obligation to perform split tunneling for VPN users.
Currently, the only way that receives the VPN client is a default route. I noticed that on site-to-site VPN and tunnels GRE, you can specify safe routes, but I can't find anything that relates to remote VPN users. This can be done on IOS without problem, but would be good for the RPS.
I'm under the latest firmware 1.01.26, so if I have not forgotten anything it would be probably for a future version?
See you soon.
Bryce
Hi Bryce,.
Nothing is overlooked, it is not possible to set up split tunneling for the VPN of the RPS server.
Kind regards
Andy
-
What is is it possible to use the acl extended for split tunneling on ASA?
I'm setting up VPN IPSEC RA on SAA and I would like to know if it is possible to use the ACL extended as part of the split tunneling?
Thank you!
Yes, you can use the extended ACL. See this example:http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-nex...
Kind regards
Averroès.
-
Web VPN/SSL - general Split Tunnel capable?
When I look through some examples of configuration for IOS Web VPN - it seems you attract to the filling of a web page of web sites that users can go to. I would be rather thin client act as client light 4.x CVPN - divided for example tunnel with access to a resource internal resource. Is this possible with Cisco VPN Web? Also - with is WebVPN any ability of the NAC?
I'm not sure IOS SSL vpn, but on the asa webvpn, there is a complete client ssl option. With this, you can either create a tunnel, or all split tunnel and the only defined networks. I hope that answers your question.
-
Best Soho - Split Tunnel VPN router
Hi - I'm looking for some advice for a soho router.
Basically the main feature, I'm looking for is to run, which I think is a VPN split tunnel, so that all internal clients route default traffic out to the gateway of the ISP. However, if the traffic is destined for a list of several specific subnets (x.x.x.x/24, y.y.y.y/24 etc.), then it should establish a tunnel to an only PPTP/IPSEC host and route remote traffic for these subnets via the tunnel. To be clear, that these subnets (x.x.x.x and y.y.y.y) is not attached to the end of the tunnel - which is a gateway device that will route them further.
I've been watching the various VPN router offers and is not clear to me if I can do it with a RV - 042, BEFVP41 or something like the other thing SRP521W I must be able to manipulate the routing tables directly on.
As an additional note, I have complete control over the end of SOHO - but simply an account at the end of the tunnel with (it is a service provider). The idea is to use public services for 90% of the traffic, but if customers want to access a specific set of addresses, it will forward this specific traffic through the tunnel.
Thanks in advance...
On current view, do not touch the RPS with a bargepole.
Adding access to additional subnets through a VPN tunnel is pretty standard, routing will be automatic if the VPN was established, but you must ensure that
1. politics VPN at BOTH ENDS allows your local subnet to access these networks
2. your subnet is not incompatible with other subnets or roads that can be used on remote networks
3. assuming you're OK so far, remote subnets must have a route is added to the default gateway to point to your subnet via intermediate networks
Good luck!
-
VPN, Internet and a Split Tunnels traffic
Please attached photo because I hope that explains what I really want to do, but here's the break down.
When a VPN Client connects to remote access to 1-ASA5510 I want all Internet traffic to send to 2 - ASA5510 instead of back to the default route. When it comes out 2-ASA5510, it passes through the content filter. 2 - ASA5510 has Split Tunnel put in place and we are trying to do away with Tunnel from SPlit.
I hope this is clear enough.
Any ideas would be helpful
Dan
Dan,
Difficult but doable! First of all, there is a nice feature in the ASA that allows configuration of remote proxy based on VPN profile by: -.
Group Policy <> attributes
use a MSIE-proxy-server method
Internet Explorer-proxy server value x.x.x.x
activate Internet Explorer-proxy local-bypass
Well Yes you guessed it - works only on Microsoft Internet Explorer.
I don't think that any policy based routing would work for you - bad luck.
But you can try another feature - traffic through the tunnel, which is normally used in the topllogy of EasyVPN: -.
Configuration of the ASA at the bottom, I probably would test this with the IP address of the 2651 router!
HTH.
Maybe you are looking for
-
Screen lock key combination does not work in the Sierra
Hello! After the upgrade to Sierra, I can switch over my screen using the command-Shift-Eject button combo. I have a Macbook that is anchored to the bottom of my desk, and security, we need to lock before leaving our office. Thanks for your help! Ger
-
When you type in window 7, one character at a time is accepted?
I like Firefox; but I'm about to get rid of it, because it gives me the hell on the windows platform 7. It seems that it was diverting, or something. I use your last set updated. What is the solution? Benny,
-
Updated until V23.0 apparently without any problem (23.0 shown on Firefox/help/in words), get the update to 23.0.1, now I install it and everything seems fine, then the next day, I still get another update query to 23.0.1. Now at least 5 iteration. O
-
Logon screen takes forever to appear after pressing Ctrl + Alt + Delete on Windows 7 Enterprise
I hope someone could help me with that. We have recently upgraded to Windows 7 Enterprise and have some problems with some of our laptops. It takes about 5-10 minutes, sometimes before the login screen appears when pressing ctrl + alt Delete, when it
-
I fogot my administrative password and I have no reset or repair disk, Windows 7
I can only use my laptop as a guest and yes I, I'm a plonker rite
